In today's increasingly interconnected world, the realm of cybersecurity has expanded beyond safeguarding data and computer systems. It now plays a critical role in ensuring public safety. Are your city's intelligent traffic systems (ITS) resilient enough to fend off cybersecurity threats? In an era where cybersecurity directly impacts public safety, proactive measures are essential to keep traffic systems running smoothly and securely. In this blog, our trusted manufacturing partner Belden helps us explore the evolving landscape of cybersecurity in the context of traffic management.
The Rise of Intelligent Traffic Systems
Intelligent traffic systems have become critical to modern society, serving as the backbone for the development of smart roads, connected vehicles, and autonomous driving.
These systems collect real-time data about local traffic, including:
-
Vehicle Types
-
Traffic Levels and Routes
-
Congestion Areas
-
Environmental Impacts
-
Road Conditions
-
Accidents
-
Toll Usage
The dilemma, however, remains that, as intelligent traffic systems become more interconnected, they also become more susceptible to cybersecurity threats. An attack on an ITS can disrupt digital roadway signage, traffic lights, toll collection, weather stations, traffic cameras, road barriers, and navigation aids. The consequences include traffic congestion, accidents, and financial losses.
Growing Threats to Intelligent Traffic Systems
The popularity of smart vehicles has only exacerbated the threats to intelligent traffic systems.
Additional threats include:
-
Physical attacks like brute force or credential guessing
-
Wireless attacks such as remote hijacking of controls
-
Network attacks involving malware installation or exploitation of software and hardware vulnerabilities
Infrastructure resiliency, which refers to the ability to withstand attacks, continues to deliver essential services, and swift recovery, which is paramount. It can mean the difference between a traffic catastrophe and an ideal traffic flow.
Cybersecurity Threat Management Tips For Intelligent Traffic Systems
While all situations vary from one another, there are several cybersecurity best practices that Belden recommends to help protect critical traffic infrastructure:
-
Risk Assessments: Understand your network's risk level and assess the state of your cyber defenses as well as evaluate the cybersecurity measures of ITS vendors/partners.
-
Identify Security Gaps: Determine where vulnerabilities or gaps exist in your system and take steps to address them.
-
Invest in Training and Awareness: Educate employees about emerging cybersecurity threats and how to respond in case of an attack.
-
Maintain Software Updates: Keep your software up-to-date and implement effective patch management to reduce vulnerabilities.
-
Create an Incident Response Plan: Prepare a clear roadmap for responding to breaches or security incidents to minimize their impact.
-
Deploy Monitoring Expertise: Ensure the ability to monitor, prevent, and detect malicious network activity, allowing for swift identification and response to attacks.
-
Create Standardized Cybersecurity Practices: Implement standardized cybersecurity practices to prepare for, respond to, and mitigate the impacts of cyber threats.
Resources to Guide Your Cybersecurity Journey
In addition to managing cyber security threats, the U.S. Department of Transportation recommends cities and businesses rely on the following resources:
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a voluntary guidance designed to help businesses understand, manage, and reduce cybersecurity threats. Consider the five elements that apply to any cybersecurity initiative:
-
-
Identify critical assets and understand the risks
-
Protect critical assets from cybersecurity threats using safeguards like security controls and protocols
-
Detect cybersecurity incidents as they occur through monitoring and detection systems
-
Respond to cybersecurity threats that arise with well-defined incident response and escalation plans
-
Recover from a cybersecurity incident and restore resilience
-
ISO/IEC 27001 Standards

The ISO/IEC 27001 Standards are designed for information security management systems to ensure information security, cybersecurity, and privacy protection. They also align with the NIST Cybersecurity Framework and provide guidance on how to implement the best practices within the people, processes, and technology pillars.
Critical Infrastructure Protection (CIP) Standards

The Critical Infrastructure Protection (CIP) Standards, distributed by NERC, are essential for implementing comprehensive physical and cybersecurity measures to safeguard critical infrastructure. By offering informed guidance in areas like control center communications, incident response, and network security, CIP Standards empower transportation agencies to make significant strides in enhancing the protection of their own critical infrastructure.
Multi-State Information Sharing and Analysis Center (MS-ISAC)

The Multi-State Information Sharing and Analysis Center (MS-ISAC) is a collaborative focused on improving cybersecurity posture in government agencies through threat prevention, protection, response, and recovery.
Collaborating for a Safer Future
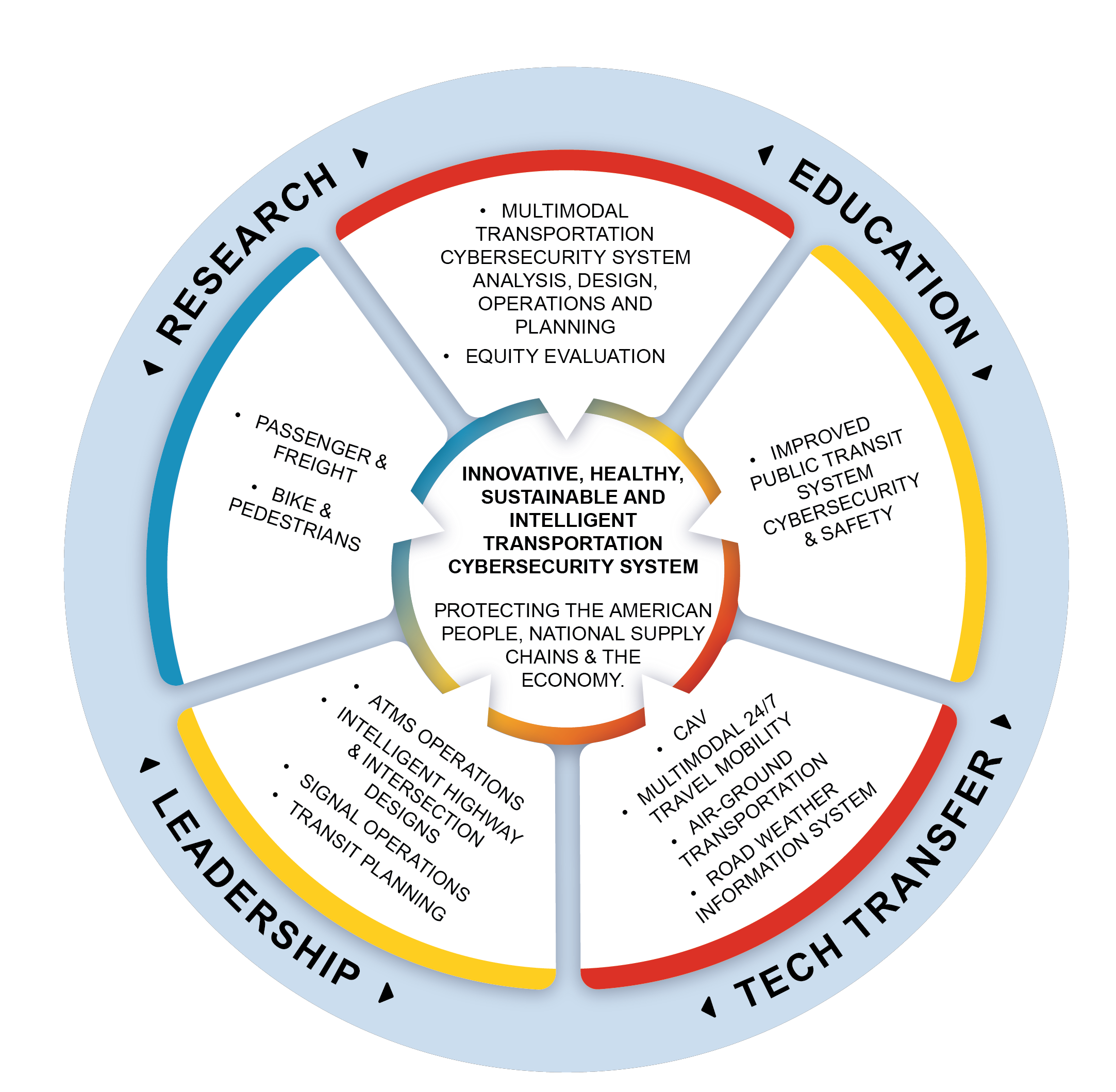
As the importance of cybersecurity in transportation and traffic systems continues to grow, resources are expanding to support these efforts. Initiatives like CYBER-CARE, funded by the U.S. Transportation Cybersecurity Center for Advanced Research and Education in 2023, aim to enhance safety by protecting vehicle control systems, detecting potential cyber incidents, and promoting industry-wide best practices.
The mission of CYBER-CARE, for example, is to develop the world’s leading innovative, healthy, sustainable, and intelligent transportation cybersecurity system and protect the American people, supply chains, public transit systems, and the economy through the safe, resilient, and sustainable movement of people and goods.
For assistance in fortifying local ITS infrastructure and protecting the community, utilize Belden cyber security experts and Accu-Tech Security Specialists. Together they bring decades of experience in safeguarding critical infrastructure from cybersecurity threats, and can bring technologies together to create a truly integrated experience.

Contact an Accu-Tech Representative to incorporate Belden solutions into your next traffic security project.





.png?width=58&height=58&name=X_logo_2023_(white).png)
